Cyber Security Essentials
Over HALF of all Cyber-Attacks Specifically Target Small Businesses.
There are new headlines about data breaches, hackings, Cyber-Attacks, and various forms of crimes against businesses. In a survey, over two-thirds of the participating businesses had suffered at least one cyber attack, while one-third had experienced the same in the last 12-months.
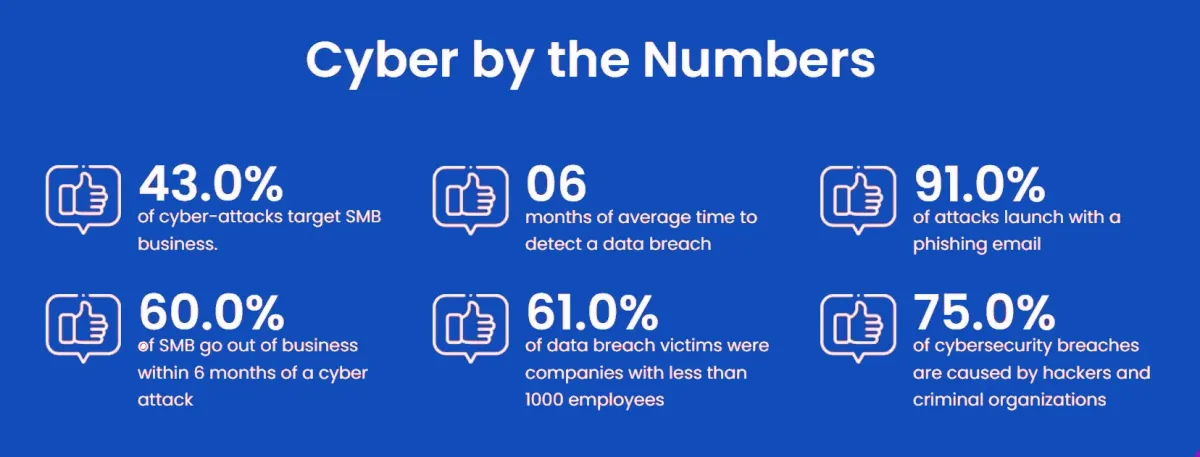
Email remains the most favored method of cybercriminals. Over 91% of attacks are initiated by email.
Traditional antivirus programs cannot identify the phishing attacks employed by hackers.
Cyber Security for Healthcare
We provide end to end cyber security support for healthcare industries.

Cyber Security for Information Business
We provide end to end cyber security support for information businesses.

Cyber Security for Financial Firm
We provide end to end cyber security support for financial industries.

Cyber Security for Insurance
We provide end to end cyber security support for insurance firm.
Only 14% of small businesses rate their ability to mitigate cyber risks, vulnerabilities and attacks.
Small businesses have no security plan in place.
Let us help you build one

91% of attacks
are launched with a phishing email
When was the last time you (or your IT Provider) ran a Third Party Cyber Risk Assessment?
Penetration testing is crucial for small businesses as it helps identify vulnerabilities in their digital infrastructure, safeguarding against potential cyber threats. By simulating real-world attacks, these tests provide valuable insights into weaknesses that could otherwise be exploited by malicious actors. Investing in penetration testing not only enhances the overall security posture but also demonstrates a proactive commitment to protecting sensitive data and maintaining customer trust.
5 Steps for Effective Cyber Defense
Risk Assessment and Asset Inventory
Implement Robust Access Controls
Continuous Monitoring and Incident Response
Regular Security Training and Awareness
Patch Management and Regular Updates
Understand Cyber Security and Learn How to Mitigate it
For a small business owner, understanding the perils of cyber risk is paramount in safeguarding the longevity and integrity of their enterprise. In an interconnected digital landscape, where businesses rely heavily on technology, the consequences of overlooking cyber threats can be severe. From financial losses and reputational damage to potential legal ramifications, the impact of a cyber incident can be devastating for small businesses.
What People Say About Our Partner Service Provider

Dianne Spessard

I am very grateful for the exceptional services that Telco United Cyber has afforded our non-profit organization, Boxer Rescue. Their expertise in computer systems, security, and backups has been invaluable to our operations

Terrell James Ramsey

We are incredibly fortunate to have partnered with Telco United Cyber.
Their expertise in running ISO audits and implementing robust cybersecurity measures has been instrumental in ensuring the safety and integrity of our client's sensitive data.

